Information Security Initiatives
As a company that plays an important role as social infrastructure in the living environment, we regard information security as one of our top management priorities and deeply recognize our responsibility to safely protect the information assets of all our stakeholders, including our customers, employees and partners.
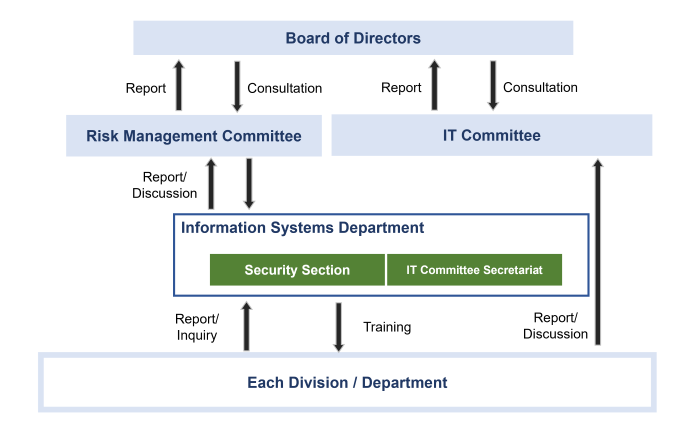
We have established a system based on our Information Security Policy and have implemented the following measures and initiatives.
Measures
Threats to information security are evolving day by day and the risk of cyberattacks and information leaks is increasing.
We have promoted following information security measures to address these risks.
Ensuring information security
We take all possible measures against security risks such as cyberattacks and information leaks to ensure the confidentiality, integrity and availability of its information assets.
In addition, we continuously review and improve our measures to enhance information security.
Compliance with laws, regulations and behavioral norms
We comply with laws, regulations, behavioral norms and internal rules relating to information security and maintain an appropriate management system.
We also regularly provide our employees with training on information security to raise their awareness.
Risk management
We properly assess and analyze information security risks and take measures according to the risks.
In this way, we minimize the risks and formulate a response plan in case of emergency.
Cooperation with stakeholders
We work together with our suppliers and partners to ensure information security.
We jointly assess risks and take measures to improve the overall level of security.
Incident response
We will respond promptly to any information security incident and work to prevent the spread of damage and its recurrence.
In the event of an incident, we will report the incident to the relevant authorities and provide appropriate information to stakeholders.
Based on these fundamental policies, we aim to fulfil our responsibilities as a social infrastructure service provider in the housing environment and achieve sustainable growth as a trusted company.
Operation System
We established an organization specializing in information security in the Company's Information Systems Department, which cooperates with security vendors to monitor and respond to security threats on a daily basis.
This enables rapid information linkage, decision-making and technical response to all incidents, not just security threats.
Information security framework enhancement
We are strengthening our governance to protect information assets and improve business continuity. In August 2025, we established the Information Security Regulations to systematize internal information-management rules, clarifying conduct standards for all staff and raising control levels.
At the same time, by strengthening training and externally sharing our expertise, we are promoting an overall improvement in the organization's security posture. Going forward, we will continue to strengthen controls and governance to address the evolving threats, aiming to realize a secure and resilient information management framework.
Major Initiatives
Below are some of our key initiatives.
Training
We utilize e-Learning to provide regular information security training for all employees. This fosters a company-wide information security culture, raises security awareness, and strengthens our ability to respond to information security risks.
We have been conducting the information security training via e-Learning every six months. In FY2024, an average of 3,400 employees participated, achieving a participation rate of 94%. During the same fiscal year, we also conducted targeted phishing simulations to strengthen practical risk-response capabilities.
In addition, to continuously raise each employee's awareness, we began delivering the e-learning course every two weeks starting in August 2025 and switched to a weekly cadence from November 2025.
By increasing the frequency and delivering it in a format that enables short, ongoing learning about the latest threats, phishing techniques, and insider-threat prevention, learning timing became more dispersed which made it easier for employees to participate in the training.
As a result, employees have more opportunities to be mindful of information security in their daily work, which has supported the ongoing development of security literacy and its integration into everyday operations.
External communications: Information security officer's appearance at an industry event
-
Our information security officer spoke at an external industry event to share our security strategy and internal training efforts. The external feedback was positive, demonstrating our approach to security and the transparency of our measures.
-

Obtaining and maintaining ISO 27001
We have obtained and maintain ISO 27001, the international standard for information security management systems (ISMS), for our operations in our information systems department.
This certification indicates that the information security management system complies with internationally recognized standards and maintains high security standards through continuous improvement.
Technical security environment development
Security measures are implemented using the latest technology.
- Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR): both provide enhanced endpoint protection and monitoring, enabling rapid detection and response to malware and unauthorized access threats.
- Attack Surface Management: through the management of the attack surface area, vulnerabilities are made visible and risks are mitigated to enhance security.
- Network monitoring: 24/7 network monitoring is in place to detect abnormal activity in real time for prompt response.
SERVICE SITES
-
- Clicking the links above will take you to the home page of each site.